CRM price optimization
Price optimization gives companies a way to apply analytics to existing CRM data to improve profitability. Companies can create prices on the fly, based on customers’ past buying history and the profitability of the product or service. Successful CRM price…
Sun rises on Java Web services
What Sun Microsystems’ Java WSDP (Web Services Developer Pack), Early Access Release 1, shares in common with IBM’s Web Services Toolkit is that neither is ready for production use. But developers who examine WSDP now will soon find themselves a…
Head in the clouds
Sun’s failure to participate in the WS-I does little to instill confidence in Web services interoperability INTEROPERABILITY HAS been the ruin of many an enterprise endeavor, and the bane of existence for most IT professionals during the years. For Web…
CTO Demo 2002 road trip
A CTO finds some interesting offerings at the Demo conference I ADMIT IT — I went to last week’s Demo 2002 conference with low expectations of what I would find. What with our dour economy and frequent media stories about…
Class System, making copies
Use the System class to copy parts of an array February 15, 2002 Q: This question seems easy, but nonetheless I have no idea how to do it. I have a byte array: a[100] . Is there a simple way…
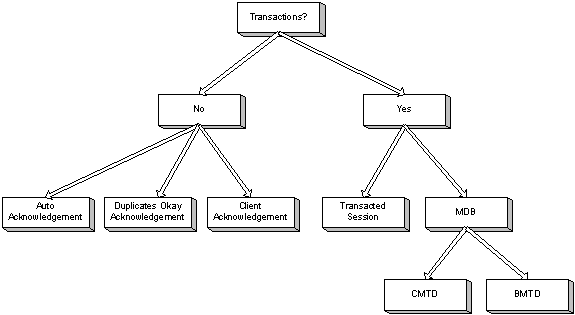
Transaction and redelivery in JMS
Make the right transaction decision for your message delivery Architecting and designing applications with the Java Message Service (JMS) requires not only knowing how to use the JMS API, but also having a solid foundation of its concepts. This article…
Mix protocols transparently in Web applications
Implement HTTP and HTTPS in a safe, flexible, and easily maintainable manner Many Web applications, especially those deployed for e-commerce, necessitate the transmission of sensitive data between the Web server and the client browser. This data could include passwords, credit…
With Liberty and single sign-on for all
The Liberty Alliance Project seeks to solve the current online identity crisis If you spend much time online, chances are you have established more than one online identity. On Yahoo!, you’re JS133xyz and on Slashdot, you’re known as KlingonB. To…
Orbix E2A Web Services Integration Platform, XMLBus Edition 5.0: Catch the services bus
Iona’s XMLBus is the first stop for business-process modeling in Web services integration In the race to Web services integration, key differentiators will come not from underlying protocols and technologies but from the ease and speed with which companies are…
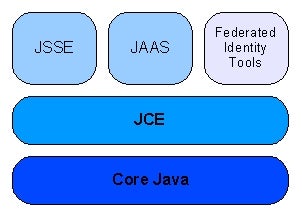
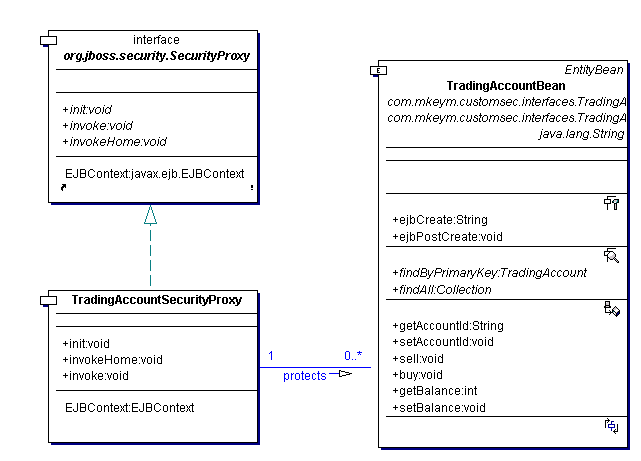
Customized EJB security in JBoss
Separate your security policy from your business logic Security is a key factor in developing many enterprise applications. Indeed, if you handle sensitive data or offer restricted services, you need a clearly defined security policy for your application and a…