Speaking on the Observer pattern
How can you use the Observer pattern in your Java design? Q: I want to use the Java Observer pattern in my project. With that in mind, can you give me some sample code to demonstrate how it works A:…
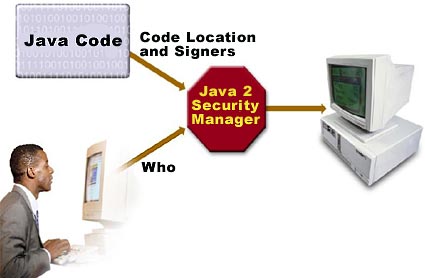
Java security evolution and concepts, Part 4
Learn how optional packages extend and enhance Java security Early on, Java security focused on resisting executable content threats — security risks caused by malicious or poorly programmed code. In this series’s previous articles, we saw how Java security evolved…
Conquer Swing deficiencies in MDI development
Add more functionality to your Multiple Document Interface (MDI) applications Developers have used the Multiple Document Interface (MDI) for many years. It provides an understandable interface for building applications that require multiple documents or windows to be hosted simultaneously within…
Java Product News (May 25, 2001)
Zero G enhances its installation platform Zero G has updated InstallAnywhere to provide increased platform support, greater installer flexibility, improved installer optimization, and a streamlined developer interface. The new InstallAnywhere 4 creates installers that can serve diverse computing environments while…
Can double-checked locking be fixed?
No matter how you rig it, double-checked locking still fails In “Double-Checked Locking: Clever but Broken,” I looked at the double-checked locking (DCL) idiom, which is recommended by a number of Java books and articles as a way to reduce…
Jato: The new kid on the open source block, Part 3
Translate XML documents into Java objects Welcome back for Part 3 in this series on Jato, the open source, increasingly capable, XML/Java translator. In Part 1, I introduced Jato and how to perform XML-to-Java and Java-to-XML transformations. Since then Jato…
Java Tip 111: Implement HTTPS tunneling with JSSE
Create your own HTTPS tunneling socket for your Java Secure Socket Extension application The Java Secure Socket Extension (JSSE) library from Sun Microsystems lets you access a secure Web server from behind a firewall via proxy tunneling. To do this,…
Master Java with these introductory books
Do these newly released books for Java beginners live up to their predecessors? Introductory Java books are a rather popular bunch. If you’re interested in Java programming, you have to start somewhere. Most people pick up at least one book…
Encapsulation is not information hiding
The principles of information hiding go beyond the Java language facility for encapsulation Words are slippery. Like Humpty Dumpty proclaimed in Lewis Carroll’s Through the Looking Glass, “When I use a word, it means just what I choose it to…
Factory methods
How do you employ factory methods to your best advantage? Q: While going through ” Polymorphism in its purest form ,” I saw the unfamiliar term factory method. Could you please describe what a factory method is and explain how…