Mapping XML to Java, Part 1
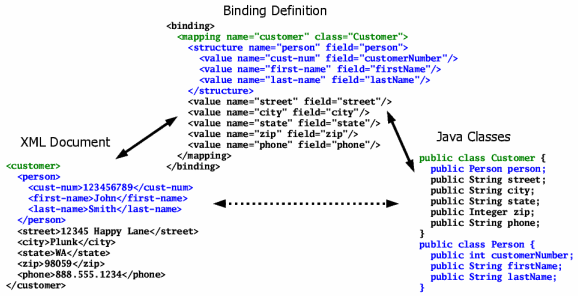
Employ the SAX API to map XML documents to Java objects XML is hot. Because XML is a form of self-describing data, it can be used to encode rich data models. It’s easy to see XML’s utility as a data…

Employ the SAX API to map XML documents to Java objects XML is hot. Because XML is a form of self-describing data, it can be used to encode rich data models. It’s easy to see XML’s utility as a data…
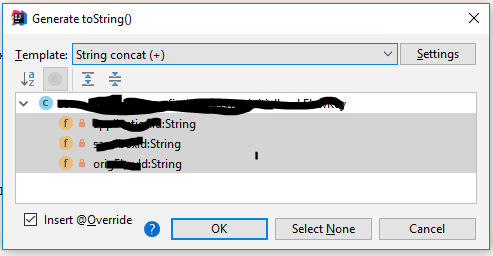
Exploit the power of Reflection and save significant coding time Developers working on large projects commonly spend hours writing useful toString methods. Even if each class doesn’t get its own toString method, each data container class will. Allowing each developer…
With Visual J++ in the dumpster, Microsoft introduces C# to fill the void July 31, 2000 — Microsoft’s new vision of the Internet is a far cry from today’s network of online content. Microsoft views the future Internet as a…
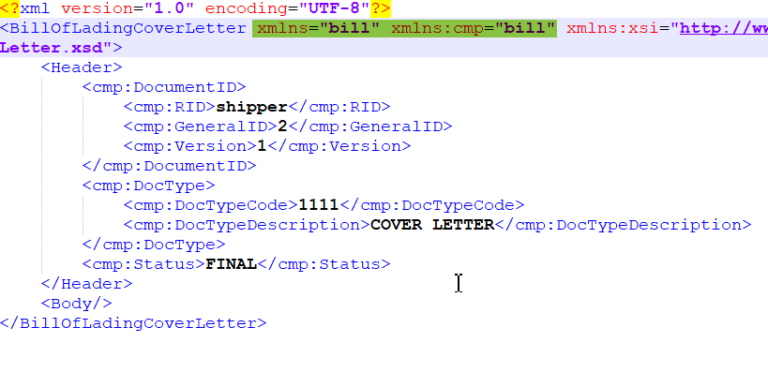
Use JDOM to create and mutate XML In Part 1 of this series, we introduced you to JDOM, and discussed how you can use it to extract information from an existing XML data source such as a file, input stream,…

Discover the ins and outs of Java security One of Java’s main features is its ability to move code over a network and run that code. Unlike other languages, Java has been designed to do this securely. Java security has…
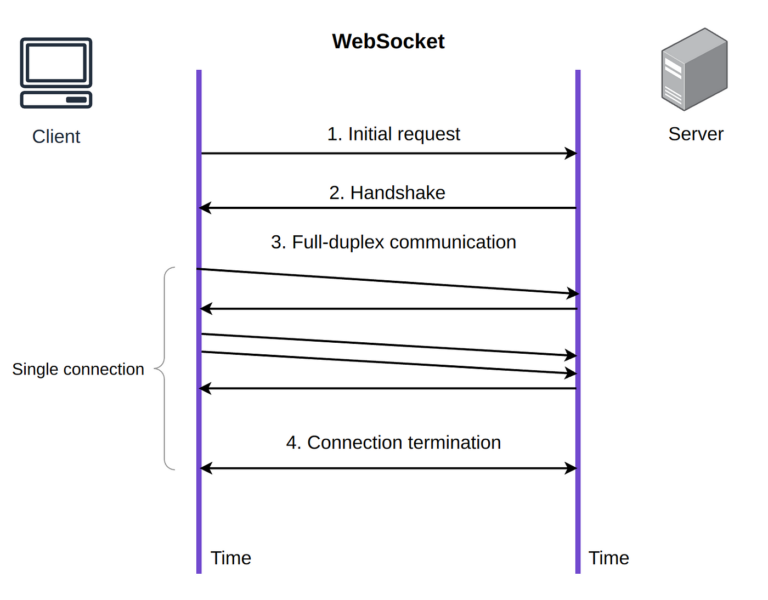
Determining the best approach when there is no client-side user In Part 1 of this series, I demonstrated two approaches to defining the interaction between a client and a newsfeed server: using documents and protocols and using objects and interfaces.…
Supplement Java’s util.zip package to make it easy to write or modify existing archives I started out this month intending to write an article about caching class loaders. I wanted to create a class loader that a client-side application could…
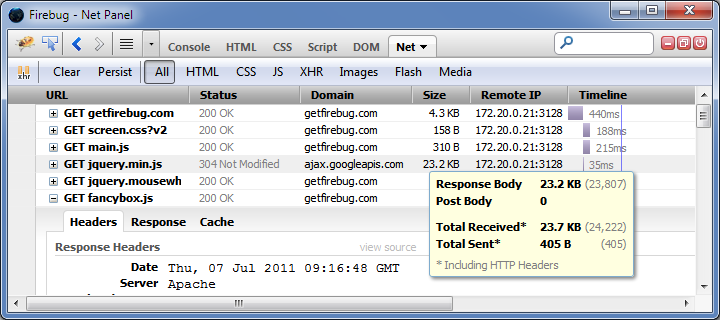
Secant’s Extreme Internet Server 3.5 Web server is good for what ails you Managing server-side Java applications is the diciest challenge in running a Website. Because your applications are coded to run on a particular server, your customer requests may…

Develop scalable and secure Java CORBA applications with Oracle8i Oracle8i features a built-in JVM, an embedded ORB (object request broker) based on OMG’s (Object Management Group) CORBA specification, and useful services such as an EJB component model. In this article,…

Decouple applications and their details using properties, XML, and cryptography When a story is reconstructed, its central plot doesn’t change. But depending on the author and audience, the plot is obfuscated by changes in context: settings, scene sequences, characters, tone,…